| Prev | Next |
Add a Port Definition
As mentioned in the Port Configuration topic, when setting up the Cloud Server you will need to define at least one Port for communication between the Pro Cloud Server and Enterprise Architect.
To add a new Port Definition:
1) Open the Pro Cloud Server Configuration Client.
2) Select the Ports tab.
3) Click on the .
4) The Add TCP Port dialog will be display. Referring to the table below, enter the Port details, then Click OK.
5) Confirm that your Firewall Settings are correct.
6) Restart the Pro Clioud Server Windows Service so that the changes take effect.
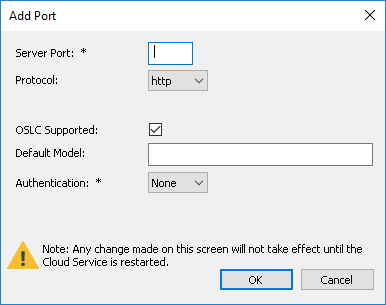
Add TCP Port
Field |
Description |
See also |
|---|---|---|
|
Server Port |
Enter the Port number to be used for Cloud Connections. Each defined Port must be unique and not used by any other service or application on the current machine. The standard HTTP Port (80) and HTTPS Port (443) are no different; if they are available, the Pro Cloud Server can be configured to use them. You can use the Windows Resource Monitor (which is accessibly via an icon on the Configuration Client 'Ports' tab) to check which Ports are already in use. Firewall Note: When changing or adding a new Port, check that incoming requests are allowed by the firewall settings at both the local machine and network levels. Wine Note: When the service is running on Wine you should not use privileged Ports - those below 1024; under Wine, most applications are only able to listen on ports above 1024. |
|
|
Protocol |
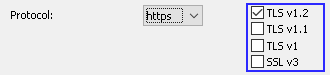
Select the protocol that the port will be configured as, options are: HTTP - The default value HTTPS - When this option is selected, you will be presented with four additional checkboxes which control the what versions of TLS (and SSL) are allowed on the given port.
Additional for HTTPS to be configured correctly a file named server.pem, must also exist in the same directory as the configuration file, and it must contain a valid private key / certificate. For more details on server.pem see the SSL Certificates section. |
|
|
OSLC Supported |
Enable this option to allow OSLC access to Models. Note, WebEA makes use of OSLC. If you intend to access Models via WebEA then this option should be enabled. |
|
|
Default Model |
Optionally, enter the name of a default model which will be used by OSLC. Typically OSLC URL's include the model name. If a default model has been specified then the model name can be omitted from the URL. |
Additional Functionality Using the Cloud |
|
Authentication |
Select the type of authentication that will be required for this Port: Model - All model connections that use the current port will be forced to request HTTP authorization using the user security defined in the Enterprise Architect model being connected to. Passwords must be explicitly and individually assigned in that model using the Maintain Users procedure; the default administrator password and any passwords imported from Windows Active Directory do not work. Note, if you are not using SSL to connect, the usernames and passwords will be sent in plain text. If the model does not have security enabled, the Cloud user is not prompted for a password. Global - Selecting this option displays an additional Global Model field. In this field enter the name of a model which will be used to provide the security profile to all connections opened with the current port. This is helpful if you want to provide multiple models but only manage one list of users. Passwords must be explicitly and individually assigned in the reference model using the Maintain Users procedure; the default administrator password and any passwords imported from Windows Active Directory do not work. Note, if you are not using SSL to connect, the usernames and passwords will be sent in plain text. Global authentication should only be used with the HTTPS protocol. |
SSL Certificates
In order for the Pro Cloud Server's internal Web Server to start a port using SSL, two individual files, cacert.pem and server.pem are required in the same folder as the Pro Cloud Server configuration file.
- cacert.pem - contains a collection of trusted certificates (in .X509 format); that is, CA certificates
- server.pem - contains a certificate and private key (in .X509 format) for your server
Sparx Systems do not supply a server.pem, because typically SSL certificates have to include the current server's details as well as individual details about your organization. Although this is an additional step, it is a particularly good idea to apply it if you are providing access to external users. Creating and signing a SSL certificate for your Cloud Server should be performed using an appropriate certificate authority (CA).
However, to help with initial setup and testing purposes, or for setups that are entirely within a closed network, you can generate your own self-signed certificate.
In general, self-signed certificates are not trusted by major browsers or operating systems and will generate errors or warnings visible to end users. See the Self-Signed SSL Certificates section on how to create a self-signed certificate.
To add trust to a self-signed certificate when it is not practical to generate globally trusted certificates, see Add Trust with a Certificate Authority (CA).
Note: If the Pro Cloud Server is started without a valid server.pem file and a port is defined with Protocol=HTTPS then the internal web server will not be able to open the port. If this situation occurs, error messages to this effect will be written to the .LOG file.
Advanced Port Configuration
Optionally, Ports can also be configured by directly editing the Cloud Server's configuration file (SSProCloud.config). This allows some additional settings which are not available in the Cloud Configuration Client.
The definition of a Port is denoted in the configuration file, with open and close parentheses, each on their own lines without any leading whitespace. Inside the parentheses contain a number of supporting options that control and limit how the port can be used. All options except SERVER_PORT are optional.
(
SERVER_PORT=804
REQUIRE_SSL=0
OSLC_SUPPORT=1
DEFAULT_MODEL=
MODEL_AUTHENTICATION=
GLOBAL_AUTHENTICATION=user model
EA_MINIMUM_BUILD=
EA_MAXIMUM_BUILD=
SSL_PROTOCOLS=SSLv3 | TLSv1 | TLSv1_1 | TLSv1_2
)
Settings Explained
Setting |
Description |
|---|---|
|
SERVER_PORT |
This option expects a numeric value (whole number) that defines a Port number; there is no default value. For example, SERVER_PORT=804 states that the Pro Cloud Server service will listen to HTTP connections on port 804. Each defined port must be unique and not used by any other service or application on the current machine. The standard HTTP port (80) and HTTPS port (443) are no different, if they are available the Pro Cloud Server can be configured to use them. Firewall Note: When changing or adding a new port, check that incoming requests are allowed by the firewall settings at both the local machine and network levels. Wine Note: When the service is running on Wine you should not use privileged ports - those below 1024. Under Wine, most applications are only able to listen on ports above 1024. |
|
REQUIRE_SSL |
This option expects either a value of 0 or 1; the default is 0. A value of 1 will enforce the use of SSL on the current port; that is, all connections must be performed using HTTPS, which is useful when connections need to be exposed on public networks. In order for the Pro Cloud Server to be able to successfully configure ports as REQUIRE_SSL=1, a file called server.pem must exist in the same directory as the configuration file, and contain a valid private key / certificate. For more details on server.pem see the SSL Certificates section. |
|
SSL_PROTOCOLS |
This option is a pipe delimited list of TLS/SSL protocol versions accepted by the port. If omitted the default of TLSv1_2 value is assumed. Valid values are "SSLv3", "TLSv1", "TLSv1_1", "TLSv1_2". For example if a port was to accept versions TLS 1.2 and 1.1 and entry should be: SSL_PROTOCOLS=TLSv1_1 | TLSv1_2 |
|
OSLC_SUPPORT |
This option expects either a value of 0 or 1, the default is 1. A value of 1 defines that connections that use the current port will be able to perform queries using the 'Open Services for Lifecycle Collaboration' standard. This is discussed further in the OSLC Requirements Management topic. |
|
DEFAULT_MODEL |
This option expects the alias of a defined database manager, or blank, the default is blank. By defining a value for this option allows a single model to be exposed on a port, making it possible to use a different port for each model. Model names are discussed further in the Connecting Enterprise Architect to a Cloud Server topic. |
|
MODEL_AUTHENTICATION |
This option expects either a value of 0 or 1, the default is 0. By defining this option as 1, all model connections that use the current port will be forced to request HTTP authorization using the user security defined in the Enterprise Architect model being connected to. Passwords must be explicitly and individually assigned in that model using the Maintain Users procedure; the default administrator password and any passwords imported from Windows Active Directory do not work. Note that if you are not using SSL to connect, the usernames and passwords will be sent in plain text. If the model does not have security enabled, the Cloud user is not prompted for a password. This option is mutually exclusive with GLOBAL_AUTHENTICATION. |
|
GLOBAL_AUTHENTICATION |
This option expects the alias of a defined database manager, or blank, the default is blank. By defining this option a single Enterprise Architect model with security enabled can be used to provide the security profile to all connections opened with the current port. This is helpful if you want to provide multiple models but only manage one list of users. Passwords must be explicitly and individually assigned in the reference model using the Maintain Users procedure; the default administrator password and any passwords imported from Windows Active Directory do not work. This option is mutually exclusive with MODEL_AUTHENTICATION. |
|
EA_MINIMUM_BUILD |
This option expects a numeric value that represents the minimum Enterprise Architect version that can connect to models using this port. The default is undefined which implies all versions are allowed. |
|
EA_MAXIMUM_BUILD |
This option expects a numeric value that represents the maximum Enterprise Architect version that can connect to models using this port. The default is undefined which implies all versions are allowed. |